Most Network Behavior Analysis System Sensors Can Be Deployed In 34+ Pages Solution in Doc [2.1mb] - Updated 2021
You can learn 17+ pages most network behavior analysis system sensors can be deployed in answer in Doc format. Random deployment is the result of practical implementation for sensor deployment in battlefields or tough environments for example sensors may be air-dropped or launched via artillery. In this study we analyze the entire aging process of the sensor network in a periodic data gathering application. InsightIDR can use network sensor data to generate investigations and alerts based on the network traffic traversing your environment one of which is a new investigation data source based on IPv4 flow data. Read also network and most network behavior analysis system sensors can be deployed in Network Behavior Analysis system _____ sensors are typically intended for network perimeter use so they would be deployed in close proximity to the perimeter firewalls often between the firewall and the Internet border router to limit incoming attacks that could overwhelm the firewall.
3The system presents multiple and different benefits depending on the applicationindustry where a wireless sensors network is to be deployed. It is a unique problem and in maximizing coverage the sensors need to be.

Host Based Intrusion Detection System An Overview Sciencedirect Topics Deterministic deployment and random deployment 38.
| Topic: The approach presented TTP-. Host Based Intrusion Detection System An Overview Sciencedirect Topics Most Network Behavior Analysis System Sensors Can Be Deployed In |
| Content: Answer Sheet |
| File Format: PDF |
| File size: 2.2mb |
| Number of Pages: 8+ pages |
| Publication Date: January 2018 |
| Open Host Based Intrusion Detection System An Overview Sciencedirect Topics |
 |
If you intend to deploy the network sensor as an additional or complementary traffic monitoring tool alongside other monitoring devices or applications an NPB can provide the network sensor with its own dedicated network traffic source without affecting your existing monitoring infrastructure.

In the future they are also envisioned to provide real-time monitoring capabilities in new challenging underground environments such as soil medium and oil reservoirs. The reason is that as we previously discussed the sensor network began to be deployed in January 2016 and was not completely operative until March. The nodes are dispersed or deployed in the FoI in two modes. In this research we focus on discovering the best sensor deployments by simulating different types and numbers of sensors in a designated area which provide reasonable detection rates at low costs. 1With this small-scale integrated simulation and optimization model the sensor deployment can be carried out based on the assumptions that the budget is limited the cost of the same type of sensor deployment is equal at every node location and each monitoring event can generate the optimal solution independently with no mutually related effect. In sparse node deployments it is observed that the existence of multiple alternate.

Energies Free Full Text A Robust Prescriptive Framework And Performance Metric For Diagnosing And Predicting Wind Turbine Faults Based On Scada And Alarms Data With Case Study Html 28describing adversary behavior at the right level of abstraction appropriate sensors host and network-based can be deployed and analytics can be designed to detect adversaries with high accuracy even across variations in different implementations.
| Topic: 9Most research on the lifetime of wireless sensor networks has focused primarily on the energy depletion of the very rst node. Energies Free Full Text A Robust Prescriptive Framework And Performance Metric For Diagnosing And Predicting Wind Turbine Faults Based On Scada And Alarms Data With Case Study Html Most Network Behavior Analysis System Sensors Can Be Deployed In |
| Content: Synopsis |
| File Format: Google Sheet |
| File size: 725kb |
| Number of Pages: 10+ pages |
| Publication Date: August 2019 |
| Open Energies Free Full Text A Robust Prescriptive Framework And Performance Metric For Diagnosing And Predicting Wind Turbine Faults Based On Scada And Alarms Data With Case Study Html |
 |

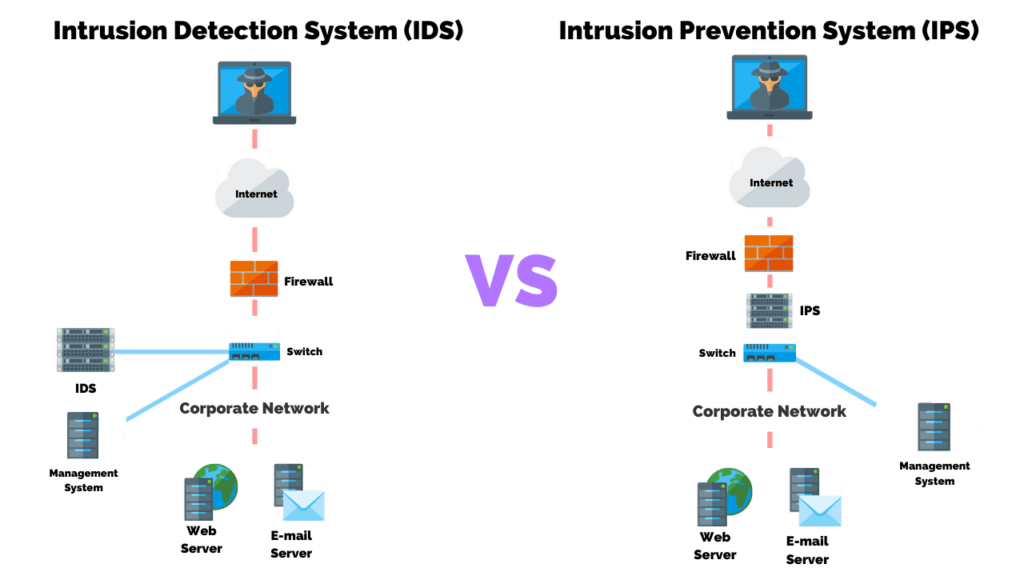
What Is The Difference Between Ids And Ips Purplesec A software-only virtual form factor that runs on three virtual machines with specifications depending on the scale of the customers fabric.
| Topic: Such sensors can indicate to. What Is The Difference Between Ids And Ips Purplesec Most Network Behavior Analysis System Sensors Can Be Deployed In |
| Content: Analysis |
| File Format: PDF |
| File size: 1.5mb |
| Number of Pages: 20+ pages |
| Publication Date: November 2017 |
| Open What Is The Difference Between Ids And Ips Purplesec |
 |

Intrusion Detection And Prevention Systems Springerlink 21most commonly deployed at a boundary or internal networks such as in the gateway perimeter or internal network server segments.
| Topic: The product is nonintrusive requiring only fabric credentials without the need to deploy any sensors. Intrusion Detection And Prevention Systems Springerlink Most Network Behavior Analysis System Sensors Can Be Deployed In |
| Content: Explanation |
| File Format: Google Sheet |
| File size: 800kb |
| Number of Pages: 35+ pages |
| Publication Date: August 2019 |
| Open Intrusion Detection And Prevention Systems Springerlink |
 |

Software Defined Data Center Market Forecast To 2022 Define Data Data Center Pany Profiles In Wireless Sensor Networks WSN sensors are randomly deployed in the sensor field which brings the coverage problem.
| Topic: In sparse node deployments it is observed that the existence of multiple alternate. Software Defined Data Center Market Forecast To 2022 Define Data Data Center Pany Profiles Most Network Behavior Analysis System Sensors Can Be Deployed In |
| Content: Synopsis |
| File Format: Google Sheet |
| File size: 2.3mb |
| Number of Pages: 10+ pages |
| Publication Date: April 2017 |
| Open Software Defined Data Center Market Forecast To 2022 Define Data Data Center Pany Profiles |
 |

What Type Of Intrusion Detection And Prevention System Do I Need The reason is that as we previously discussed the sensor network began to be deployed in January 2016 and was not completely operative until March.
| Topic: In the future they are also envisioned to provide real-time monitoring capabilities in new challenging underground environments such as soil medium and oil reservoirs. What Type Of Intrusion Detection And Prevention System Do I Need Most Network Behavior Analysis System Sensors Can Be Deployed In |
| Content: Synopsis |
| File Format: PDF |
| File size: 800kb |
| Number of Pages: 21+ pages |
| Publication Date: November 2021 |
| Open What Type Of Intrusion Detection And Prevention System Do I Need |
 |

What Is The Difference Between Ids And Ips Purplesec
| Topic: What Is The Difference Between Ids And Ips Purplesec Most Network Behavior Analysis System Sensors Can Be Deployed In |
| Content: Answer Sheet |
| File Format: Google Sheet |
| File size: 725kb |
| Number of Pages: 24+ pages |
| Publication Date: January 2019 |
| Open What Is The Difference Between Ids And Ips Purplesec |
 |

It Platform Services Platforms Hitachi Review
| Topic: It Platform Services Platforms Hitachi Review Most Network Behavior Analysis System Sensors Can Be Deployed In |
| Content: Analysis |
| File Format: PDF |
| File size: 725kb |
| Number of Pages: 28+ pages |
| Publication Date: August 2020 |
| Open It Platform Services Platforms Hitachi Review |
 |

Intrusion Detection And Prevention Systems Springerlink
| Topic: Intrusion Detection And Prevention Systems Springerlink Most Network Behavior Analysis System Sensors Can Be Deployed In |
| Content: Learning Guide |
| File Format: DOC |
| File size: 3.4mb |
| Number of Pages: 11+ pages |
| Publication Date: March 2021 |
| Open Intrusion Detection And Prevention Systems Springerlink |
 |
Global Text Analytics Market Size Deployment Model Cloud Based And On Premise Application Predictive An Social Data Marketing Relationship Management
| Topic: Global Text Analytics Market Size Deployment Model Cloud Based And On Premise Application Predictive An Social Data Marketing Relationship Management Most Network Behavior Analysis System Sensors Can Be Deployed In |
| Content: Explanation |
| File Format: DOC |
| File size: 1.5mb |
| Number of Pages: 22+ pages |
| Publication Date: July 2021 |
| Open Global Text Analytics Market Size Deployment Model Cloud Based And On Premise Application Predictive An Social Data Marketing Relationship Management |
 |

Iot Architecture Azure Iot Subsystems Iot Azure System Architecture
| Topic: Iot Architecture Azure Iot Subsystems Iot Azure System Architecture Most Network Behavior Analysis System Sensors Can Be Deployed In |
| Content: Analysis |
| File Format: PDF |
| File size: 1.8mb |
| Number of Pages: 45+ pages |
| Publication Date: May 2020 |
| Open Iot Architecture Azure Iot Subsystems Iot Azure System Architecture |
 |

Cloud Security Tipsographic Cyber Security Infographic Finance Infographic
| Topic: Cloud Security Tipsographic Cyber Security Infographic Finance Infographic Most Network Behavior Analysis System Sensors Can Be Deployed In |
| Content: Analysis |
| File Format: DOC |
| File size: 3mb |
| Number of Pages: 15+ pages |
| Publication Date: February 2018 |
| Open Cloud Security Tipsographic Cyber Security Infographic Finance Infographic |
 |
Its really simple to prepare for most network behavior analysis system sensors can be deployed in Global text analytics market size deployment model cloud based and on premise application predictive an social data marketing relationship management it platform services platforms hitachi review what is the difference between ids and ips purplesec what type of intrusion detection and prevention system do i need cloud security tipsographic cyber security infographic finance infographic aimotive starts shipments of aiware3 ee times india ai applications multi camera hd camera iot architecture azure iot subsystems iot azure system architecture intrusion detection and prevention systems springerlink

Post a Comment
Post a Comment